How to recover a lost password
Summary
Starting with v2.04, Private Disk has a new feature – password recovery. Its purpose is to give you a chance to access the encrypted files if the password was somehow forgotten. The option is located on the "Recovery" tab of the main window. Switch to that tab, and click "Password", choose the character set and the length of the password, then click "Ok" to open the password recovery window.
How it works
The program performs a so-called "brute-force attack", trying all the possible combinations of characters, until the correct keyword is found. From the mathematical point of view, the program performs an enormous amount of operations, to be exact n^k operations; where n is the length of the character set, and k is the length of the password.
Q&A
The risk is dramatically minimized, provided that you follow our recommendations on choosing a strong password .
No, it does not. The complexity of the 256-bit AES encryption algorithm is a good shield against that. Let's study a simple example.
The password is "mypass", it has a length of 6 characters, and it uses 5 distinct letters. If you try to crack your own password, there will be 5^6=15626 options to choose from. By making the password one character longer (adding one of the letters already in use), the figure changes, 5^7=78125. As you can see, a small increment of the input leads to the tremendous growth of the output. Graphically, it looks like this:
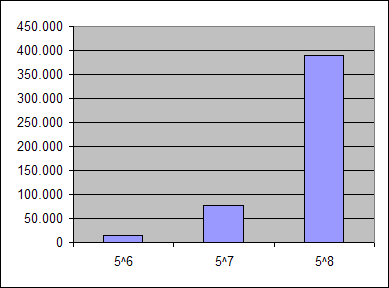
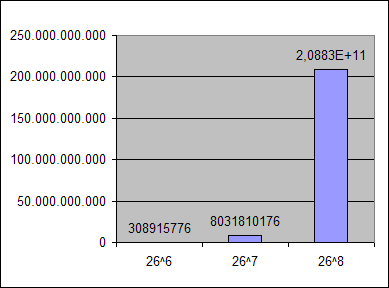
From the attacker's point of view, the situation is totally different. The person doesn't know the characters you used, hence they will probably assume that small letters were applied. This means that there will be 26^6=308915776 attempts. If you make the password one character longer, the previous value increases to 8031810176 (adding 7722894400 more operations!)
Length 23 characters 63 characters
5 1h 50m 6d
6 1d 20h 1yr
7 46d 68yrs
8 3.3yrs 4032yrs
9 90yrs 252000yrs
10 2304 …
… … …
16 1872000 yrs …
26 characters – the small letters of the English alphabet
63 characters – small letters, caps, digits, space
Note, that the values are halved, in order to reflect the average situation - an attacker may find the password without having to try all the values.
As you can see - the time intervals are far beyond the human potential. Therefore, we conclude that the password can be found in a short time only if the brute-force attack is conducted by the owner of the files - the person who knows which symbols are used, this will effectively cut off a lot of redundant computations.
Another important aspect is that the brute-force attack will only look for passwords of the specified length. In other words, if you set the length to 7 characters, the program will not examine shorter passwords, gradually increasing the length until it equals 7. This significantly reduces the attacker's chance to find the password. The person will have to perform several attacks, and if they are unsuccessful, it is unclear whether the problem was in the length, or in the symbols that were not included in the character set.
This makes it even more complicated. An attacker will have a lot of planning to do before actually telling the computer to perform the attack. On the other hand - it is a quick solution for the authentic owner of the files, since the correct length is known.
Examine our recommendations on choosing a strong password:
1. You need to choose a password that’s long enough. There’s no minimum password length everyone agrees on, but you should generally go for passwords that are a minimum of 12 to 14 characters in length. A longer password would be even better.
2. Include Numbers, Symbols, Capital Letters, and Lower-Case Letters: Use a mix of different types of characters to make the password harder to crack.
3. Don't choose a Dictionary Word or Combination of Dictionary Words. Any word on its own is bad. Any combination of a few words, especially if they’re obvious, is also bad.
4. Don’t Rely on Obvious Substitutions: Don’t use common substitutions, either — for example, “passw0rd” isn’t strong just because you’ve replaced an o with a 0.
Yes. A complex password can be easily spotted if someone watches you while typing it very slow. Therefore you must make sure that there are no people behind your back when you type, and do your best to type fast and correct - so that you will not need more than one attempt to enter the password (this will give "anonymous watchers" a second chance). Another measure is to keep the password in your memory and not on a separate piece of paper in your pocket, or any location other than your head.. You should not mention it to anyone either.
We had a great number of requests in which customers who forgot their passwords desperately wanted to recover their information. If this feature didn't exist - some software developer would certainly create a utility that does the job for money. We decided not to burden our clients with extra-expenses, hence this option is not provided in a separate tool, but it is integrated into the application itself. Its purpose is to help our users solve their problems on their own. Plus you can use it as an audit-instrument (i.e. try to brute-force your own password using an extended character-set, and decide whether the chosen password is good enough or not).
Links
- Private Disk Light: 128-bit encryption – free disk encryption software
- Private Disk: 256-bit encryption – full-featured, user-friendly and reliable disk encryption software
- Private Disk Multifactor: 256-bit encryption – disk encryption software with smart card/USB flash drive authentication
- Private Disk FAQ: Our encryption software in questions and answers
- Secrets Keeper : 256-bit encryption – disk encryption software with smart card/USB flash disk authentication and seamless integration into Microsoft Office products
List of Services
-
Missing RegistrationList Item 1
Contact us if you did not receive the registration key after your purchase
-
Berofe you contact usList Item 2
How to help us help you
-
Knowledge baseList Item 3
Learn how to protect your data and use our software
-
List of supported devicesList Item 4
USB flash disks, smart cards, tokens, biometric devices
-
Device compatibility
Will your hardware device work with Dekart software?
-
Documentation
User guides for Dekart products
